The use of two-factor authentication is being more and more common in the bid to make data more secure from potential hacks.
As a reflection of this TimeTrak from version 19.2 onwards supports the use of two-factor authentication.
How to setup two-factor authentication
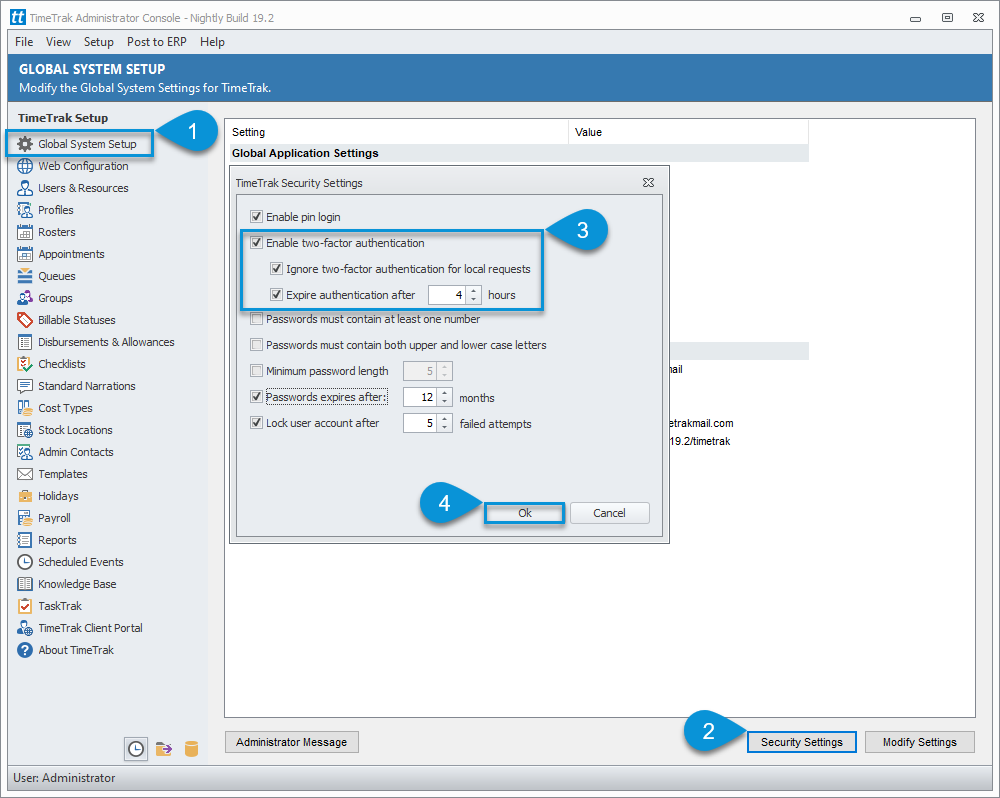
In TimeTrak from 19.2 onwards, there is a new Security Settings section with in the admin console.
Select Security Settings and enable the new setting “Enable two-factor authentication” as per below:
There is also a sub setting “Ignore two-factor authentication for local requests”.
It is recommended that this is enabled if using two-factor authentication. If this is enabled, then users will not be required to “authenticate” when they are within the network.
An additional sub setting is “Expire authentication after”. If this is enabled and a logged in user is “idle” for the set amount of hours entered against this setting, they will be prompted to re-authenticate.
This is a useful for users who may be accessing TimeTrak outside of their network as the login will “expire” after the set amount of hours ensuring your data is kept secure.
TimeTrak has hardcoded “local requests” to be within the below IP ranges:
- 10.0.0.0 to 10.255.255.255
- 172.16.0.0 to 172.31.255.255
- 192.168.0.0 to 192.168.255.255
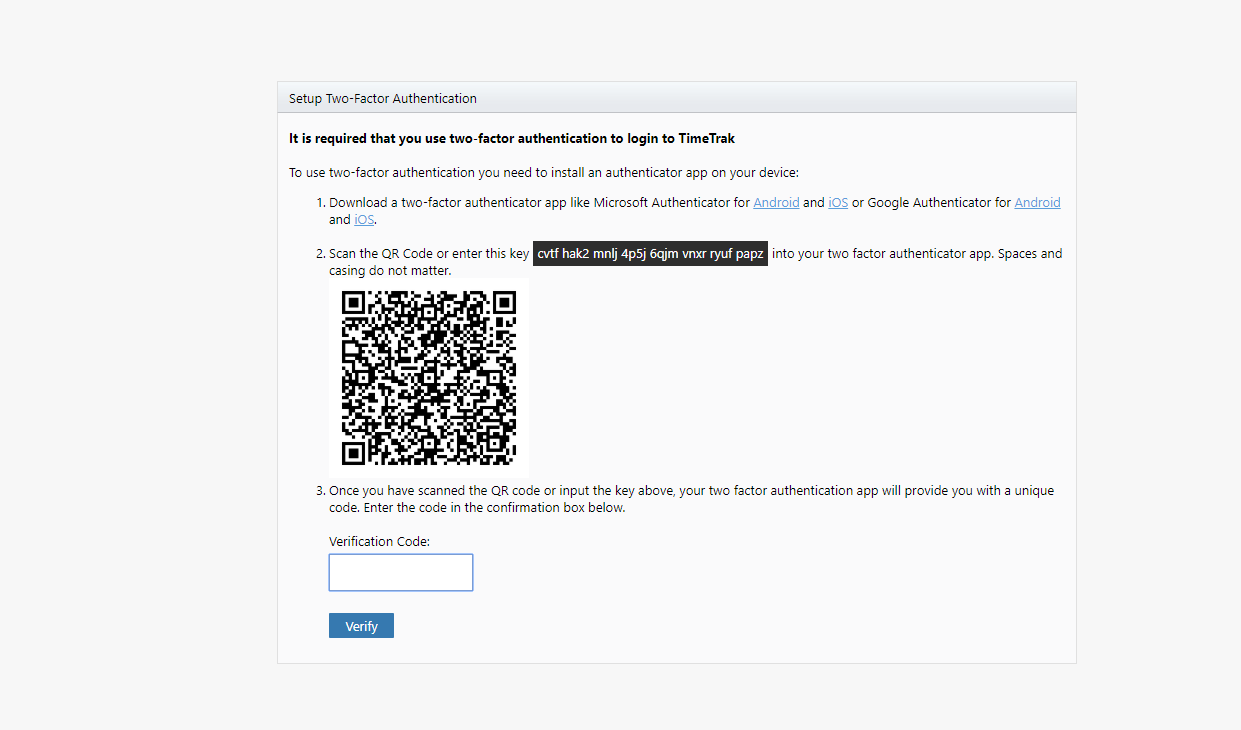
Once these settings are enabled, when users log in to the TimeTrak websites (both Professional and Mobile), as per below, they will be unable to do anything until they have “authenticated” by entering the code in the two-factor authentication application of your choice.
Professional Website:
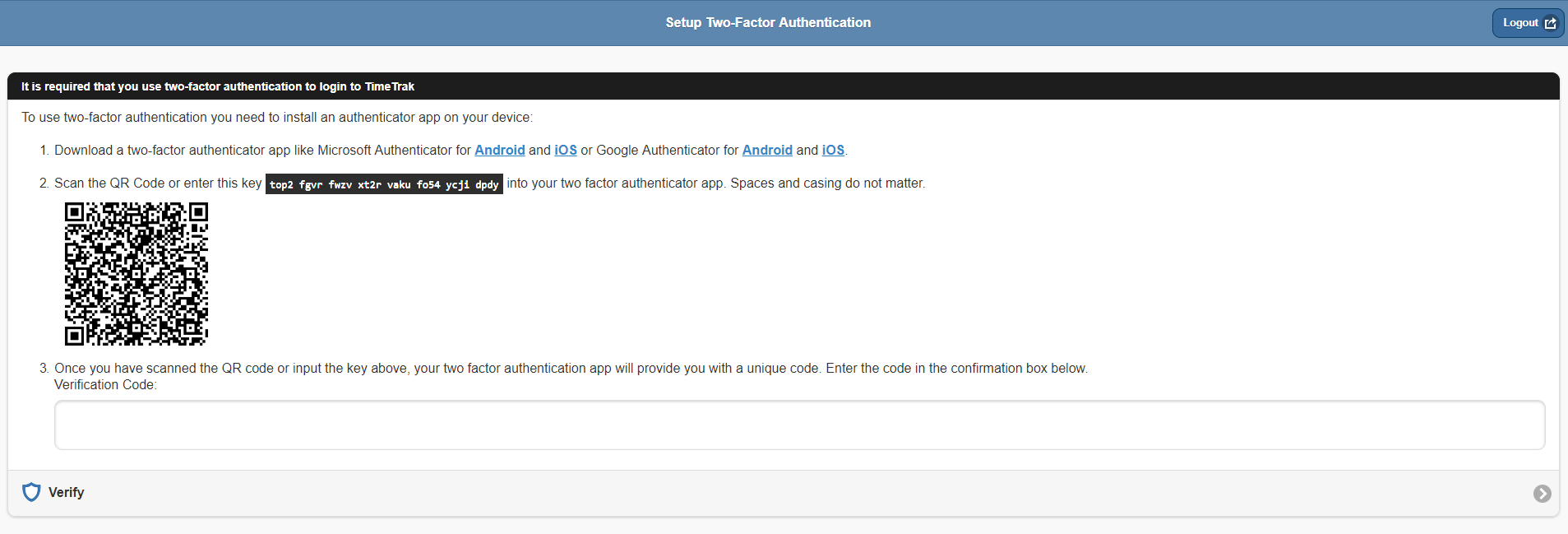
Mobile Website:
In this example, the “Microsoft Authenticator Application” was used.
Click Add Account as per below:
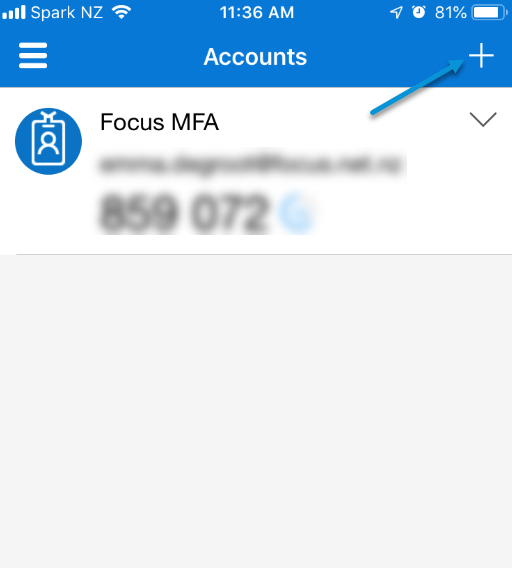
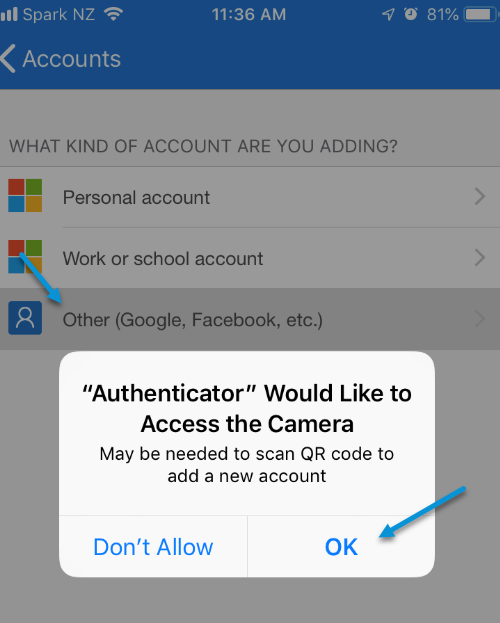
Select other as per below and allow the application access to use the camera:
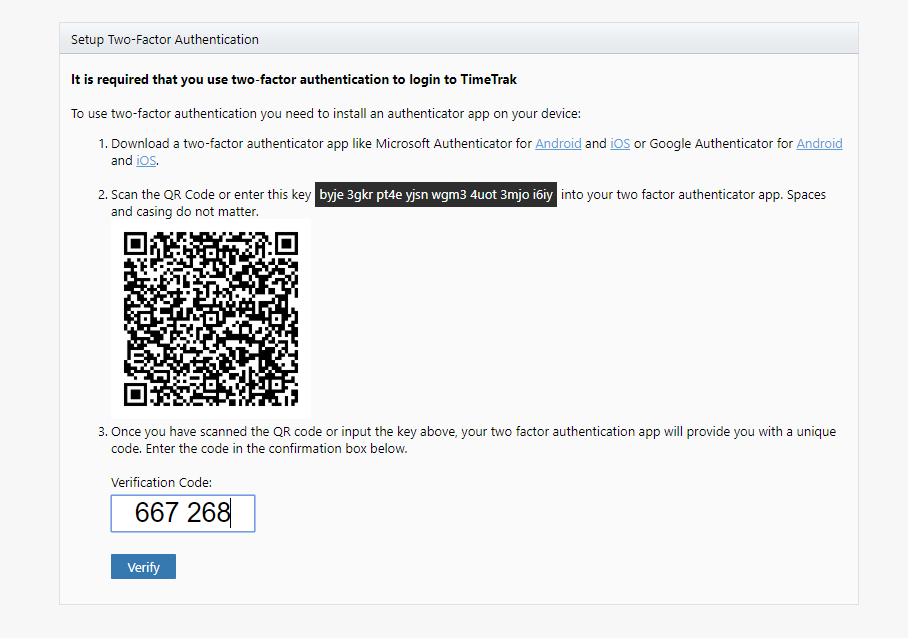
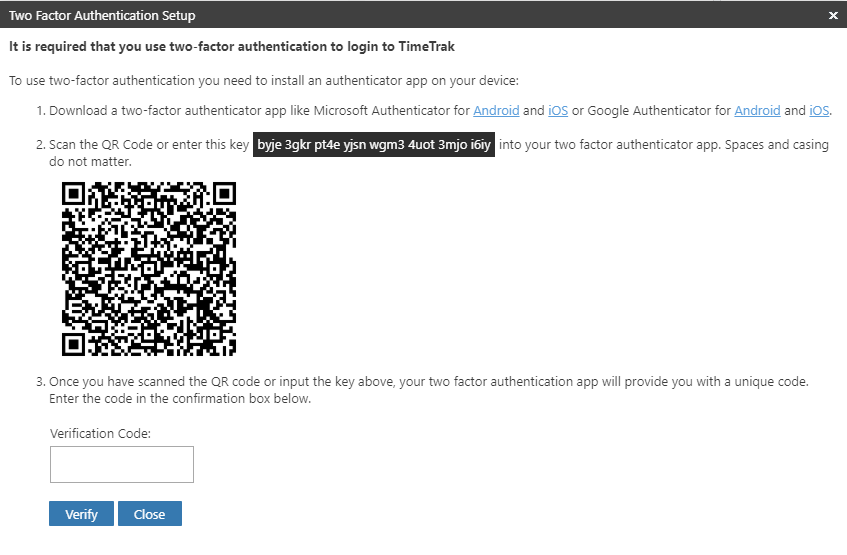
Scan the QR code on the TimeTrak login screen, this will then generate the new account “TimeTrak” as per below:
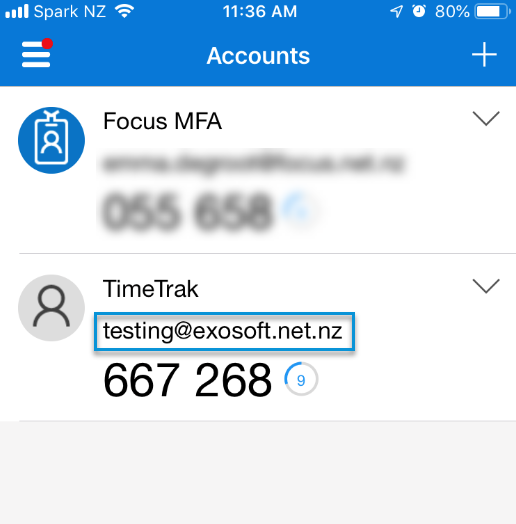
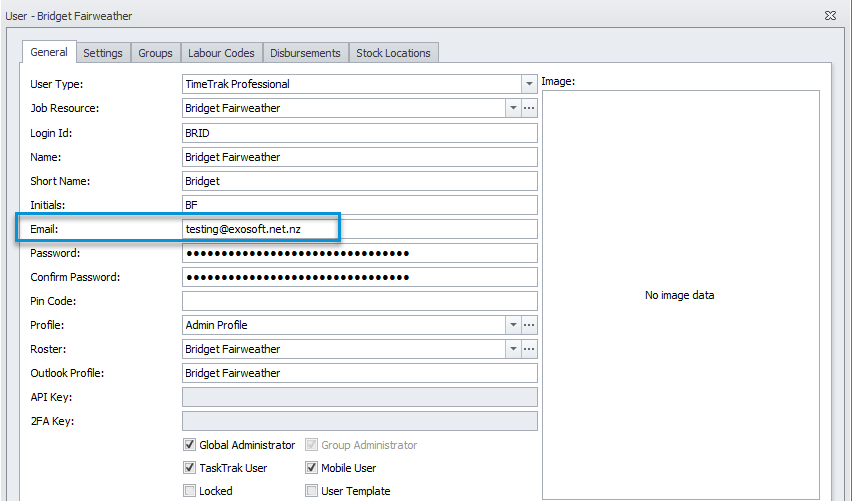
Note: the email address displayed is the email address specified against the user in the TimeTrak Admin Console as per below:
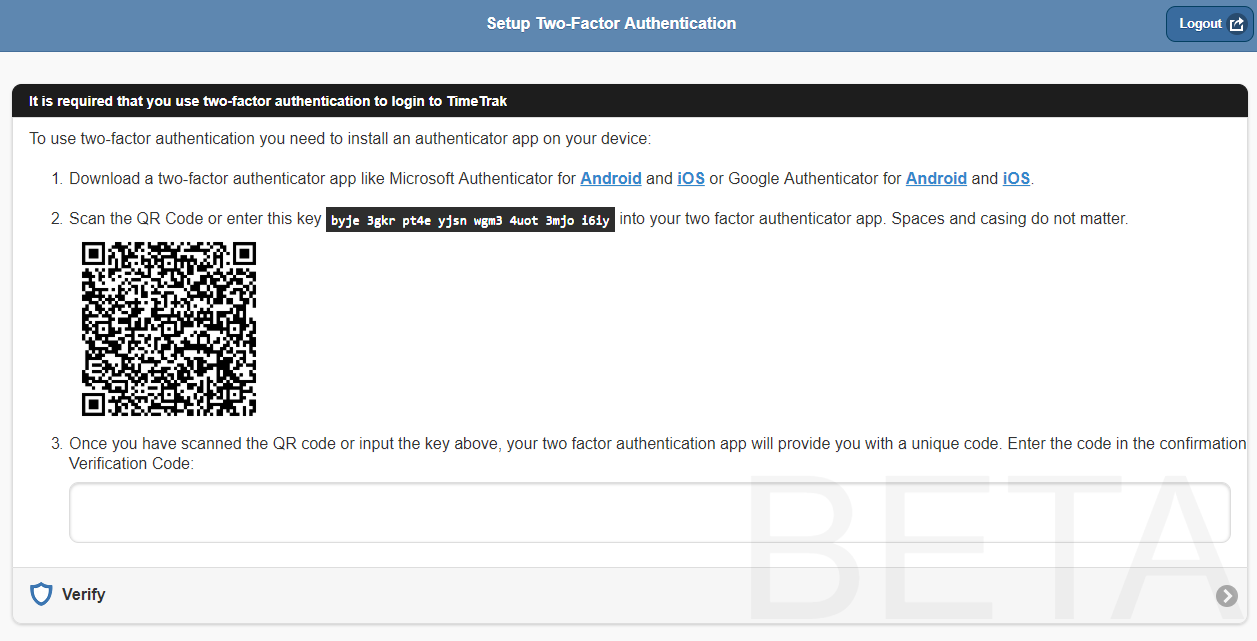
Enter the code from the authentication application into the login screen prior to the code expiring and click “Verify” as per below:
Once authenticated you will be logged into TimeTrak as per usual.
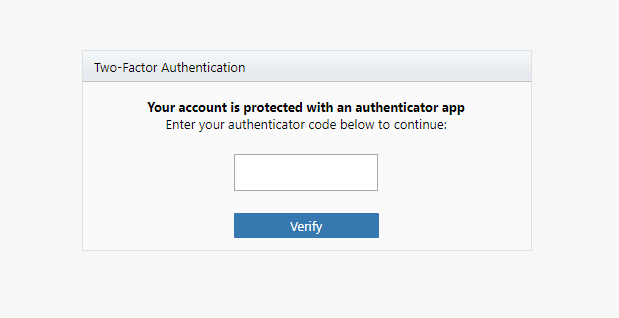
Once this setting is enabled and authentication has been configured, when logging into TimeTrak only when outside of the network if “Ignore two-factor authentication for local requests” is enabled, will users be prompted to enter their authentication code as per below.
If “Ignore two-factor authentication for local requests” is not enabled, then users will be prompted to enter their code every time they login.
TimeTrak Professional:
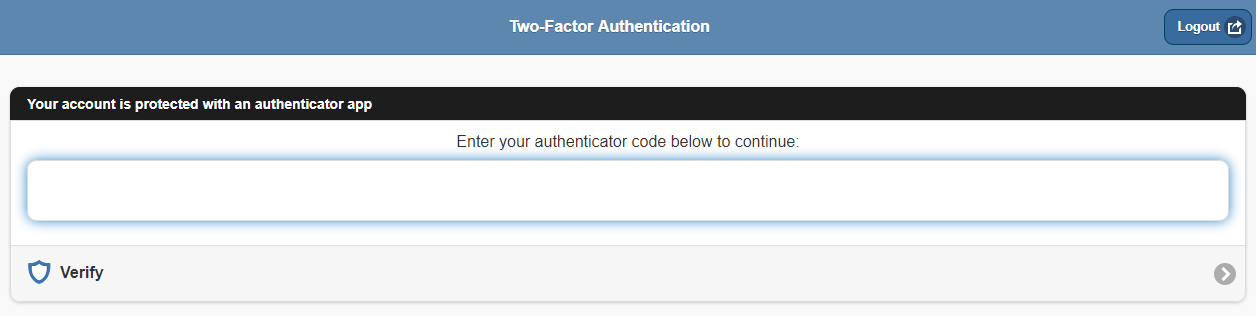
TimeTrak Mobile:
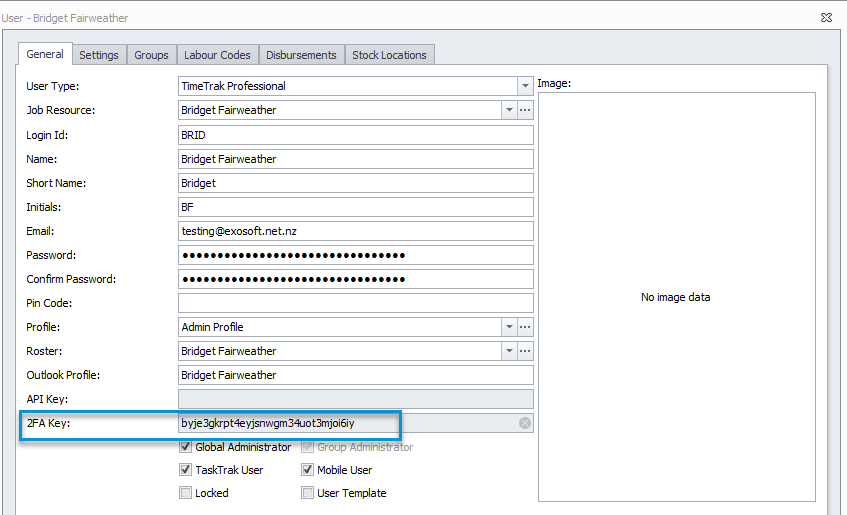
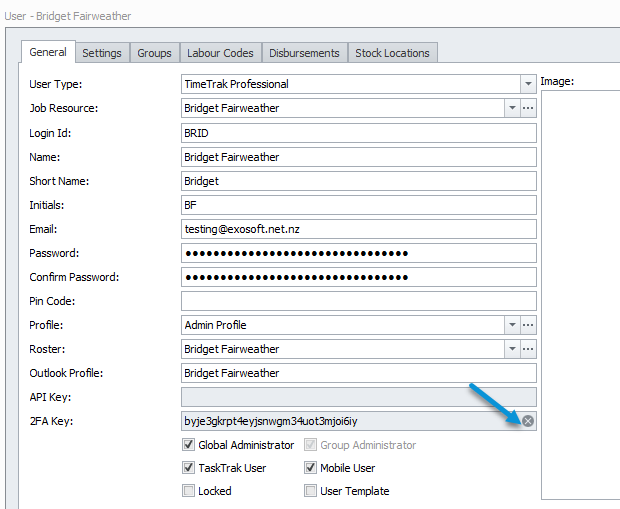
Users who have two-factor authentication setup will then have a 2FA Key specified against them as per below:
If for some reason the user has the application un-installed from their phone or has a replacement phone and authentication needs setup again, they could do this by logging into the TimeTrak website within the network if “Ignore two-factor authentication for local requests” is enabled and go to “Two Factor Authentication Setup”.
In TimeTrak Professional, this is located under Personalise as per below:
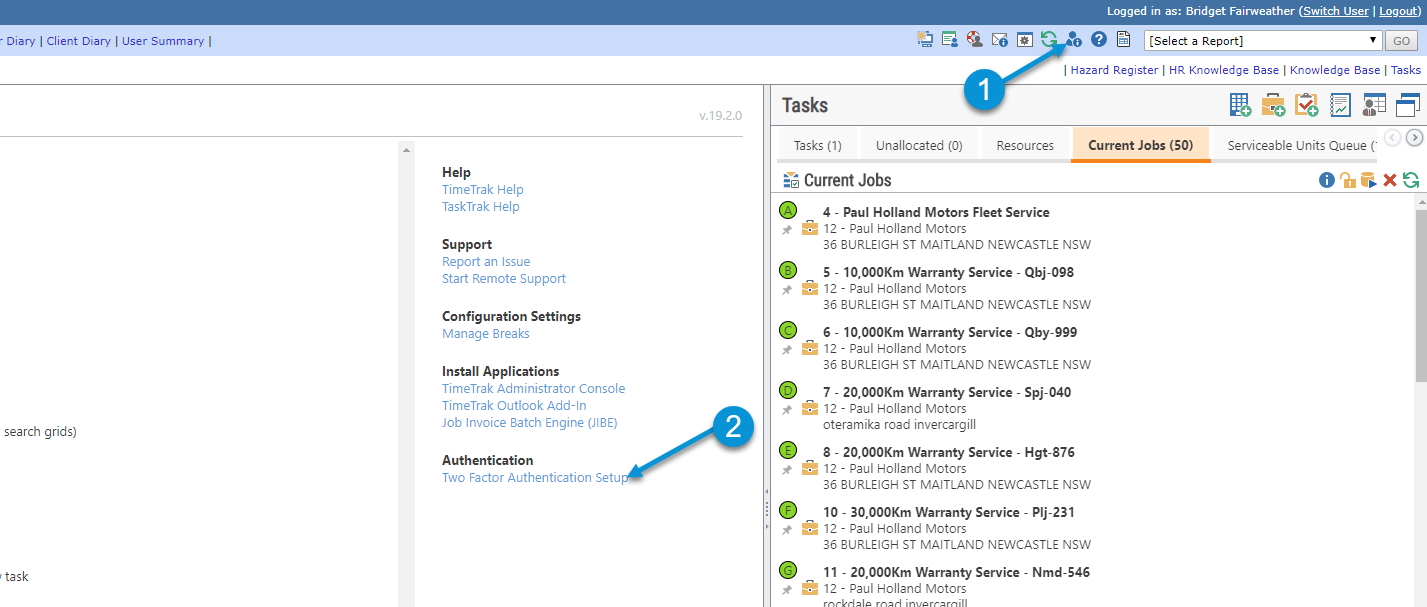
This will prompt the setup screen where the previous steps can be completed:
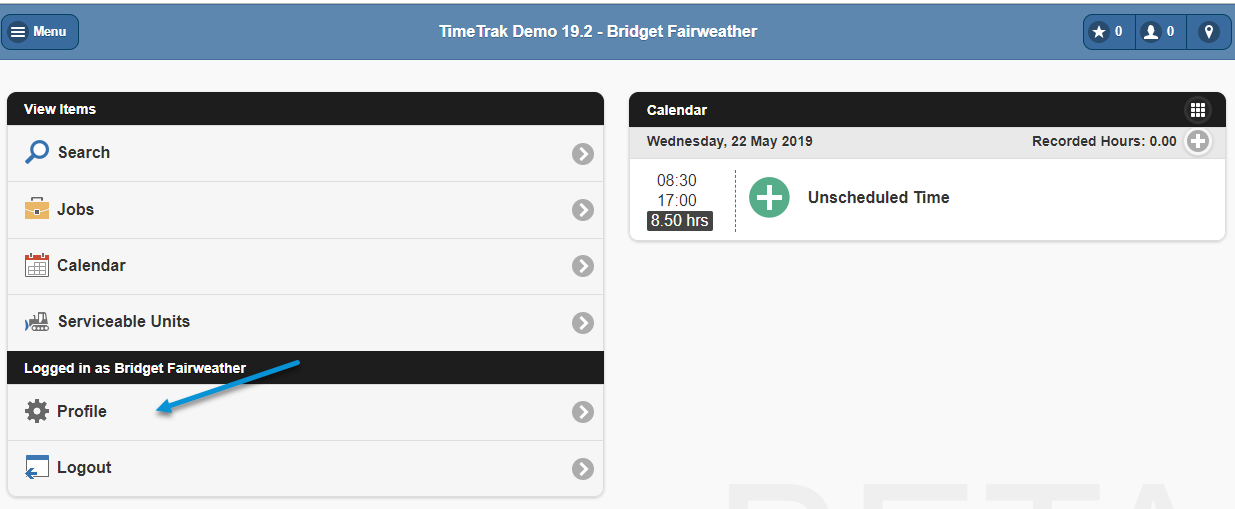
In TimeTrak Mobile, this is located under the profile icon as per below:
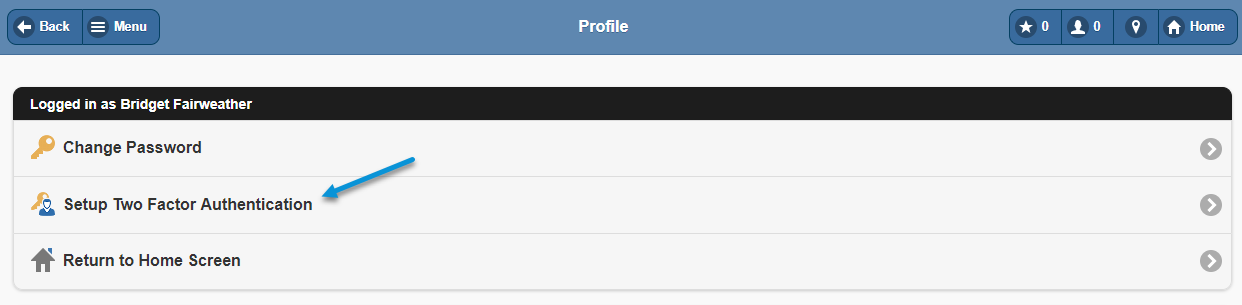
This will prompt the setup screen where the previous steps can be completed:
If the user is outside the network, or “Ignore two-factor authentication for local requests” is not enabled then the 2FA Key against the user in the TimeTrak Admin Console can be cleared as per below, which will prompt the user to complete authentication again on login.
Password Requirements, Expiry and Locking Accounts:
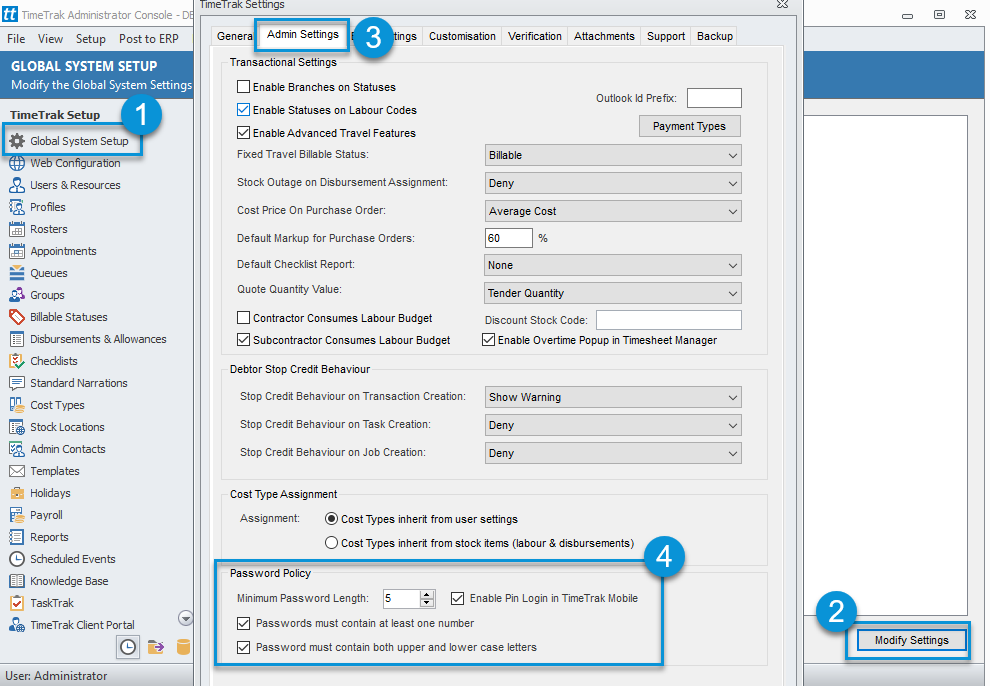
In TimeTrak 19.1, the ability to set the databases Password Policy and enable pin login to TimeTrak was located in the TimeTrak Admin Console under Admin Settings in Global System Setup as per below:
In TimeTrak 19.2, all these settings have now been moved to the new settings section “Security Settings” as per below:
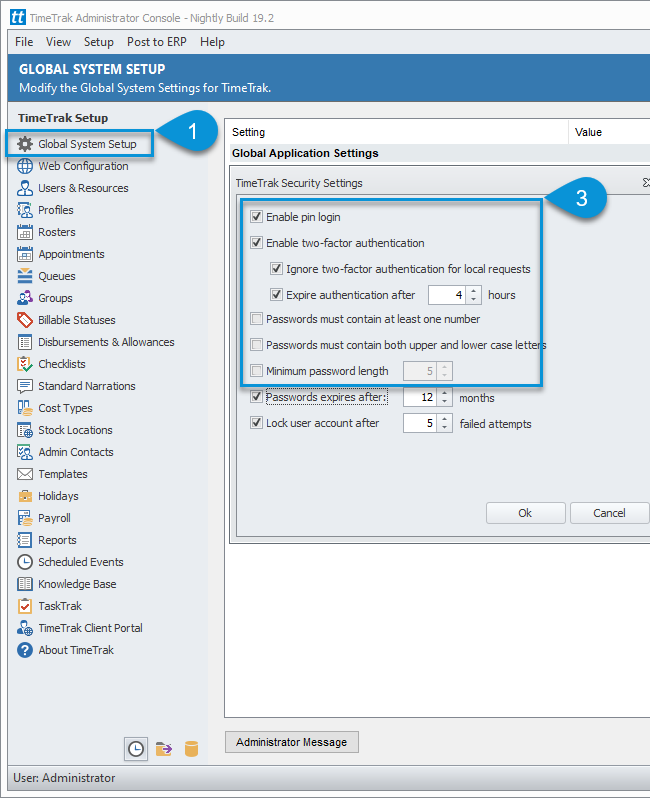
In addition to the ability to enable two-factor authentication in TimeTrak from version 19.2, there is also the ability to set passwords to expire as well as lock accounts after a specified number of failed attempts.
There are two additional settings to control this, these are located under the new Security Settings section with in the TimeTrak Administrator Console as per below:
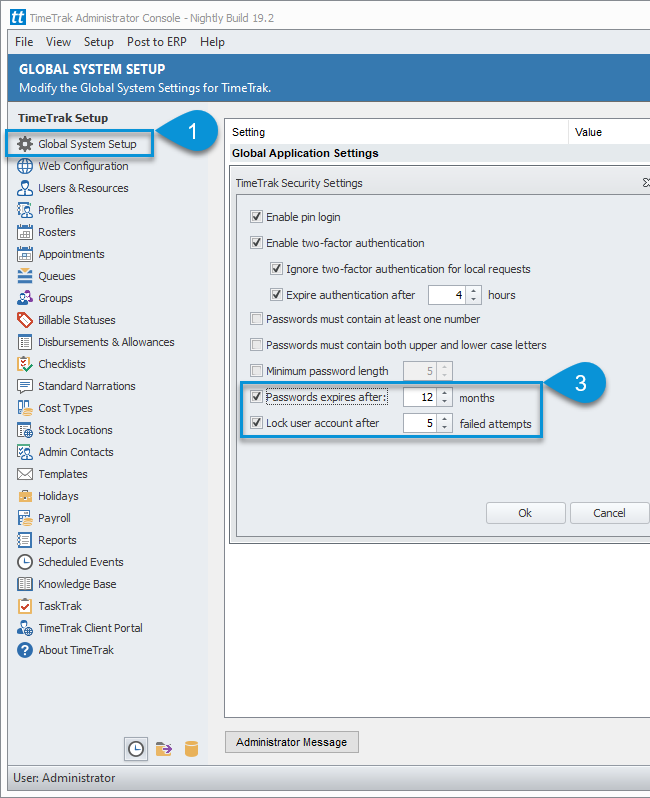
It is recommended that all of these settings are enabled to ensure your data is as secure as it can be.
Set Passwords to expire
When “Passwords expires after ___ months” is enabled, after a user’s password is changed, the “PasswordExpiryDate” on the user table in TimeTrak will be updated with the current date plus the amount of months the password expiry date is set to.
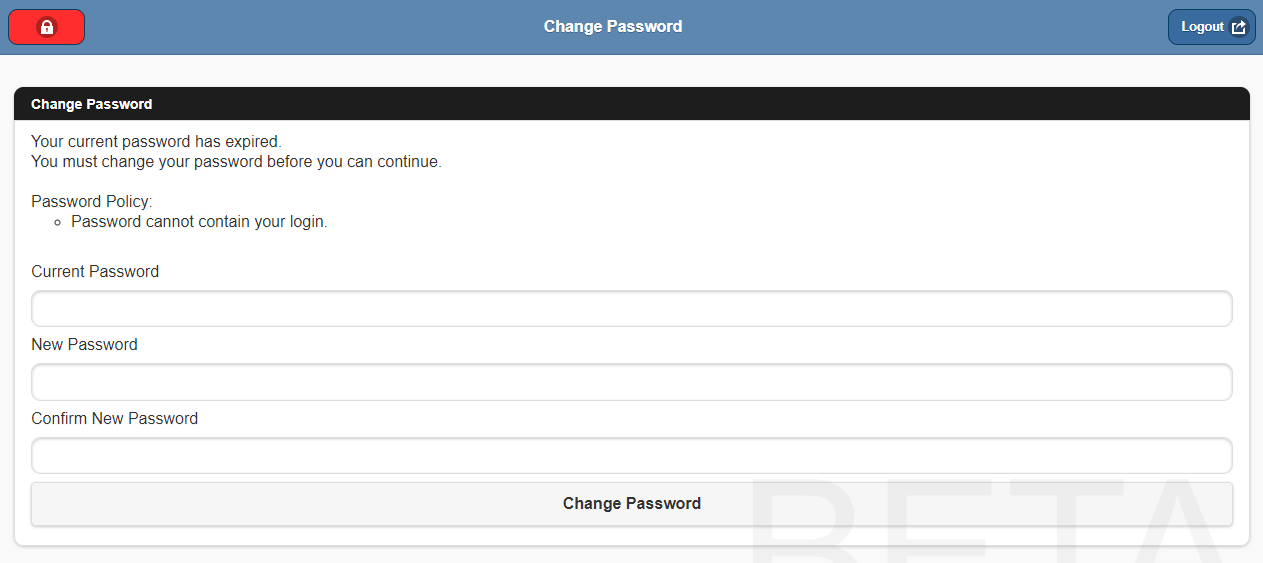
Once the Password expiry date is met and the user logs in they will be advised that their password has expired and be prompted to enter a new one as per below:
Please note: TimeTrak also prevents the ability to set a user’s password as “Password”. Users will be allowed to save this password change but will be prompted to update it on trying to login using it as it does not meet the password policy requirements.
TimeTrak Professional:
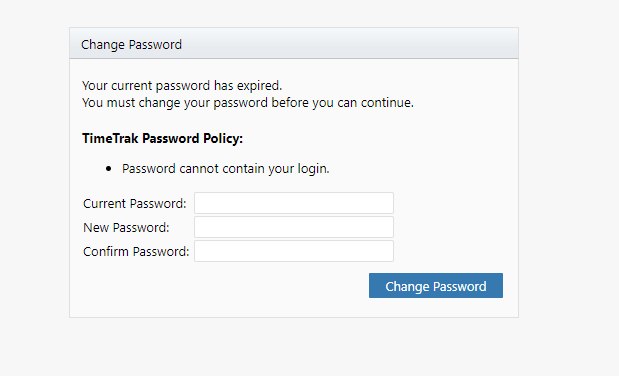
TimeTrak Mobile:
Lock users accounts
When “Lock user account after ____” is enabled as per below and a user enters their password incorrectly the amount of times which is set as per below consecutively (in this case 5).
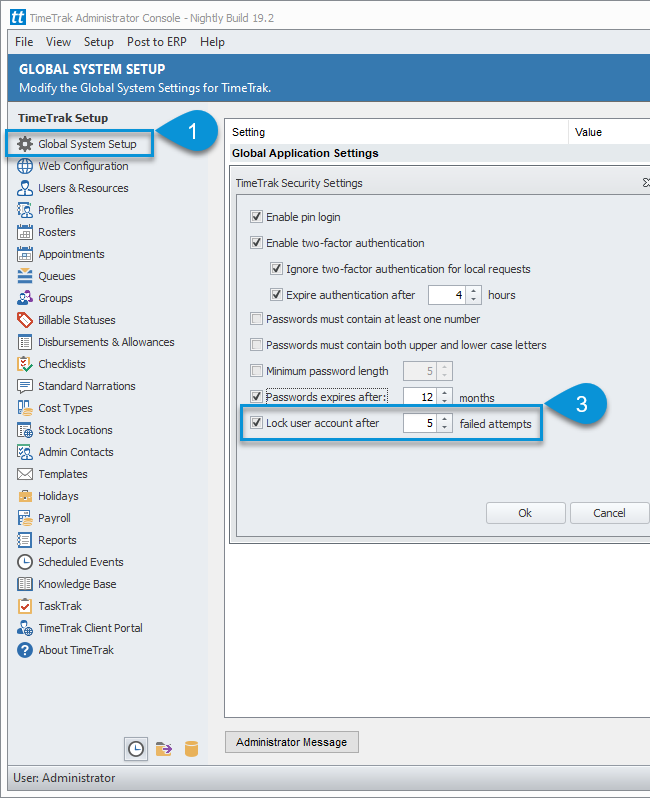
The user will be notified that their account is locked due to too many failed login attempts.
TimeTrak Professional:
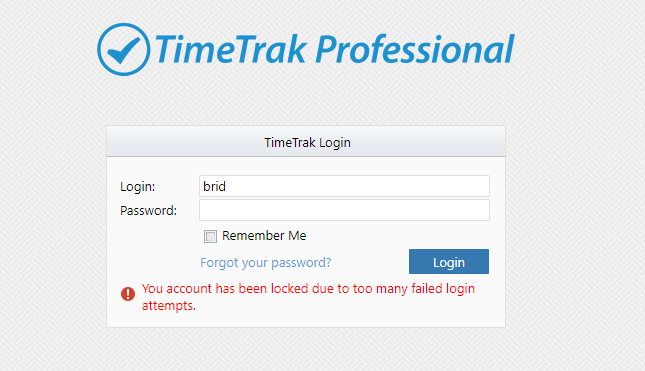
TimeTrak Mobile:

TimeTrak Admin Console:
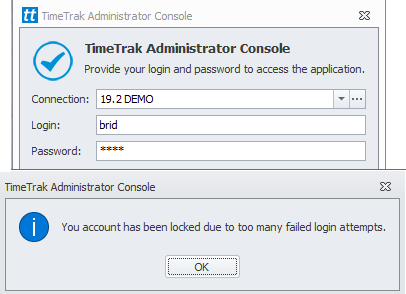
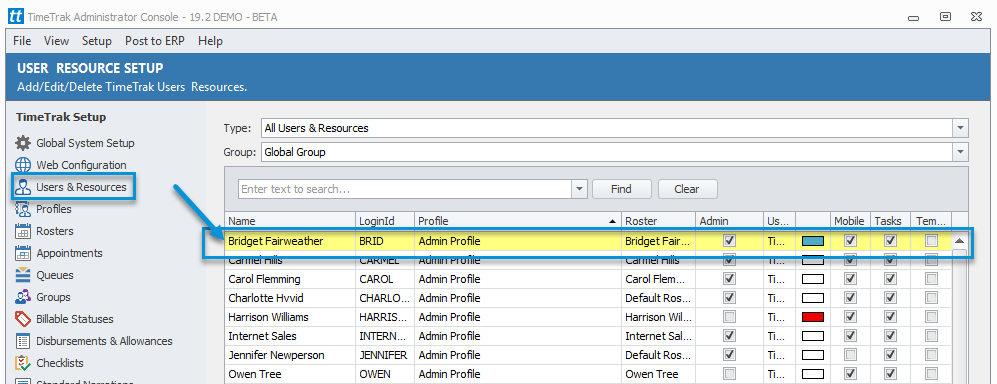
Another user with access to the Admin Console will need to login and go to the Users section, as per below users which are locked display in yellow in the user grid:
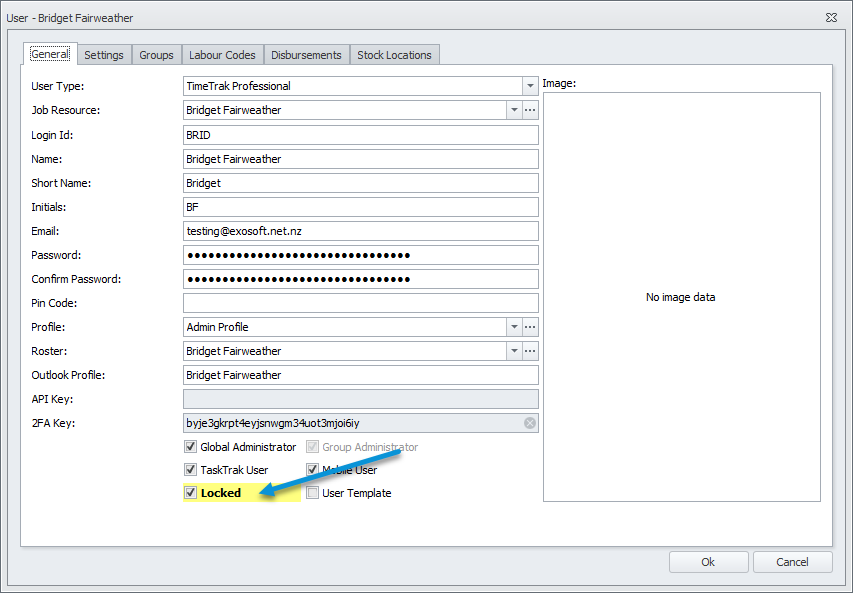
The user will have the “Locked” setting enabled as per below, this will need to be disabled to allow the user to login again.
Please note: this setting does not apply to Client Portal logins, they can enter their password incorrectly as many times as they like without their account being “locked”.
Note: they have the ability to reset their password via the login screen if they have forgotten this which will send a password reset email to the email address against the contact in Exo.